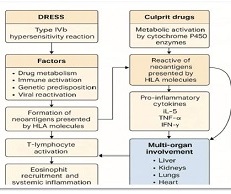
INFORMATION SECURITY AND CYBER SECURITY
Downloads
In the era of digital transformation, the dependence on information technology services and products has increased significantly. Accordingly, the challenges in information security and cyber security have increased. Social distancing, while playing an important role in containing the spread of COVID-19, increases the risk of infected workstations, unauthorized access, data leakage, malicious code execution, and all the types of risks that come with working in a vulnerable environment. Computer security, cyber security or information security - protection of computer systems and control points of networks from its interference, unauthorized use or damage to hardware, software and electronic data, as well as from destruction and violation of the services they provide to users. This area is becoming more and more important for computer systems, the Internet and wireless networks such as Bluetooth and Wi-Fi. Because of its complexity, in terms of politics and technology, cyber security is also one of the main challenges in modern life. Cyber security is one of the most important fields in today's world. This branch is connected with such demanding professions and specialties as: security analyst, security engineer, security architect, security administrator, security specialist, consultant, etc.
Types of Malware -
- Malware (Malware);
- computer virus;
- mobile media means;
- Trojan (Trojan Horse);
- rootkit;
- Backdoor (Backdoor);
- Worm (Computer worm);
- Keylogger (Keylogger).
In 2003, the computer virus Slammer penetrated the management system of the electric distribution network and slowed down its operation, which also caused the speed of management to slow down. As a result, even a small incident like a tree falling on a power line can set off a serious chain reaction. In particular, in the US state of Ohio, the voltage began to change, and the equipment, which was installed to prevent the cascade effect, failed to isolate the high voltage area in time. As a result, 8 US states, 2 Canadian provinces (a total of 50 million people) were left without electricity and services dependent on it. This example shows what can result from a little carelessness, ignoring security issues, in the digital information space. Today, cyber security is at risk like never before.
Downloads
დ.გულუა, კიბერუსაფრთხოება, ბიზნესისა და ტექნოლოგიების უნივერსიტეტი, 2020წ.;
ა.დანელიანი, კიბერუსაფრთხოების უზრუნველყოფა ეროვნულ და რეგიონულ დონეზე, საქართველოს, სომხეთისა და აზერბაიჯანის მაგალითზე, სამაგისტრო ნაშრომი, 2019წ;
https://matsne.gov.ge/ka/document/view/5263611?publication=0
D. Gulua, Cyber Security, University of Business and Technology, 2020;
A. Daneliani, Ensuring cyber security at the national and regional level, on the example of Georgia, Armenia and Azerbaijan, Master's thesis, 2019;
https://matsne.gov.ge/ka/document/view/5263611?publication=0

This work is licensed under a Creative Commons Attribution-NonCommercial-NoDerivatives 4.0 International License.