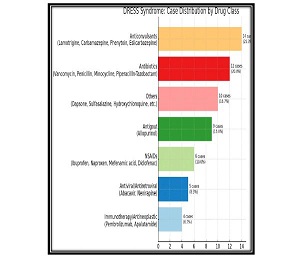
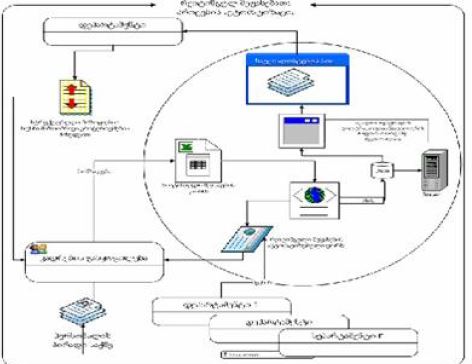
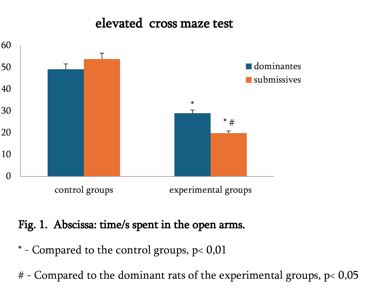
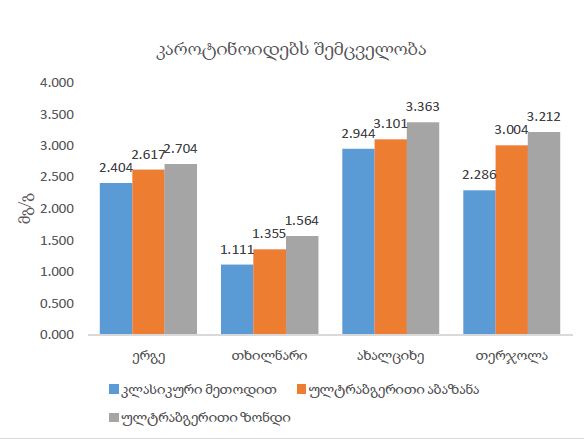
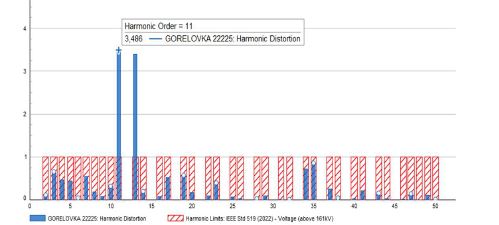
Review and analysis of existing systems for detecting network attacks
Downloads
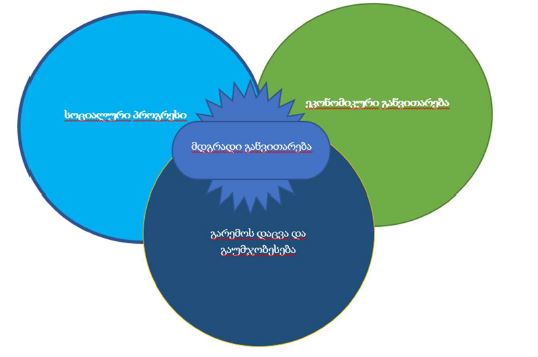
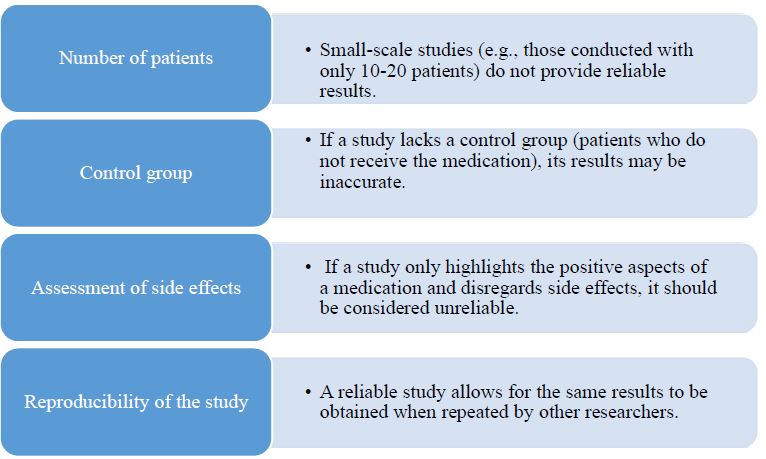
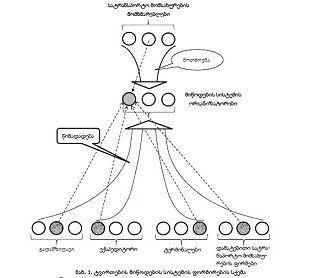
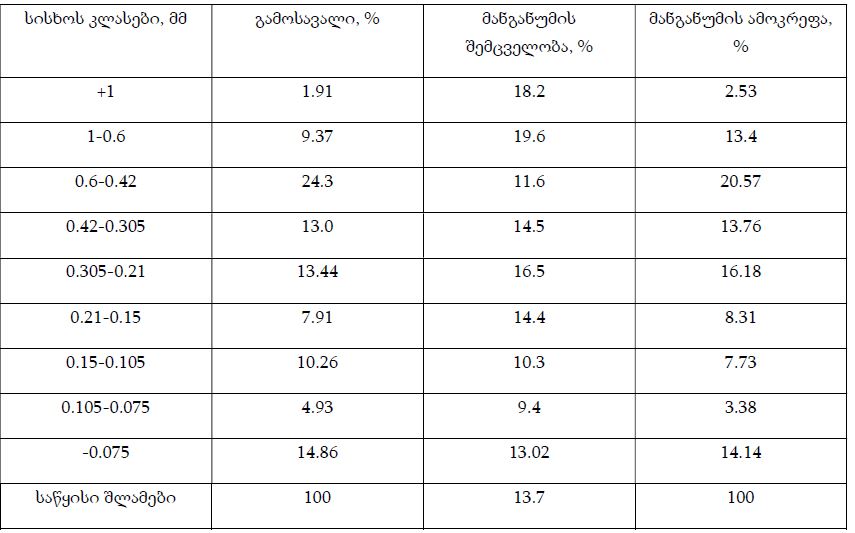
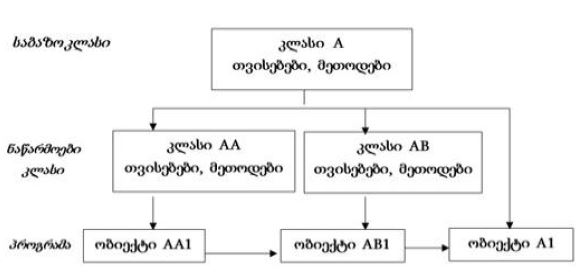
Research in the field of detection of attacks on computer networks and systems has been conducted for a long time. Signs of attacks have been investigated, methods and means of detecting unauthorized access attempts have been developed and used through security systems, both on the Internet and at the local, logical and physical levels. Commercial intrusion detection systems by various foreign companies (Cisco, Snort, ISS Real Secure, etc.) are widely represented in the local market. Many local researchers use architectural analogues and typical solutions of already known systems. In recent years, the number of different types and methods of organizing unauthorized intrusion into computer networks has increased dramatically. Therefore, intrusion detection systems have become an important component of organizations' security infrastructure. This is facilitated by the appearance of a large number of literary sources, complex approaches and methods for detecting attacks in information systems. The purpose of the review of the existing network attack detection systems presented in the paper is to investigate the functionality of currently available IDSs and to reveal the shortcomings of the used attack detection methods and the disadvantages of their usability. Realizations of existing attack detection systems can be divided into two parts: research and commercial products. Each new research project is distinguished by the introduction of new methods of analysis and new approaches to the study of monitoring objects, although they quickly become obsolete. Commercial projects (such as ISS Real Secure, Symantec Network Security, Cisco IPS, etc.) remain relevant longer due to the support of manufacturers. The manufacturers provide ongoing customer support, new attack research, and signature updates. Therefore, it can be noted that most of the commercial research results are abuse detection systems, namely handwriting systems. Intrusion detection systems IDS (Intrusion Detection System) represent software and hardware-software solutions, where the processes of collection, storage and analysis (monitoring) of events occurring in a computer system or network are automated, and these events are independently analyzed in search of signs of information security violations. These protection systems exist as programs that can display a message that a network attack has occurred at that moment. Systems that are used to detect network attacks solve only one specific task - protection from an external attacker who tries to bypass protection systems and gain access to a local local network, but the problem of protection from internal threats remains an unsolved task. All known IDS are conditionally divided into three classes: - Network IDS (Network-based IDS, NIDS); - Nodal IDS (Host-based IDS, HIDS); - Hybrid IDS (Hybrid IDS). Node IDS can be further divided into two subclasses: system level IDS and application level IDS (application-based IDS).
Downloads
ქართველიშვილი ი., ოხანაშვილი მ., ჩორხაული ნ. ქსელური შეტევების აღმოჩენის არსებული მეთოდების მიმოხილვა და ანალიზი. საერთაშორისო სამეცნიერო-პრაქტიკული კონფერენცია „თანამედროვე გამოწვევები და მიღწევები ინფორმაციულ და საკომუნიკაციო ტექნოლოგიებში - 2023“ საქართველო, თბილისი 12-13 ოქტომბერი, 2023 წელი. გვ.410-416.
Ledesma, Josue. “IDS vs. IPS: What Is the Difference?” Inside Out Security, October 23, 2018. https://www.varonis.com/blog/ids-vs-ips.
Andersen, I. (2023, November 22). Top 10 Most Common Types of Cyber Attacks. Https://Blog.netwrix.com/. https://blog.netwrix.com/2018/05/15/top-10-most-common-types-of-cyber-attacks/#Birthday%20attack
Copyright (c) 2024 Georgian Scientists

This work is licensed under a Creative Commons Attribution-NonCommercial-NoDerivatives 4.0 International License.